State‑Sponsored Hacking: What It Is and Why It Matters
When talking about state‑sponsored hacking, cyber operations carried out or backed by a government to achieve political, economic, or strategic goals. Also known as nation‑state cyber attacks, it blends intelligence gathering, digital sabotage, and profit‑driven crime. A key trait is the use of nation‑state cyber operations, coordinated campaigns that leverage state resources, legal cover, and often advanced hacking tools. These campaigns don’t stay limited to data theft; they regularly spill into cryptocurrency mining illicit activities, unauthorized mining farms that harvest coins using cheap, stolen electricity or hijacked devices. The profit helps fund further espionage while skirting international sanctions. In fact, sanctions evasion, methods used to bypass economic restrictions imposed on hostile states often fuels these illicit mining operations, creating a feedback loop where cyber‑crime finances more cyber‑crime. This web of motives makes state‑sponsored hacking a distinct threat that blends political objectives with pure financial gain.
Real‑World Examples and How They Shape the Crypto Landscape
One of the most vivid illustrations comes from Iran’s Islamic Revolutionary Guard Corps (IRGC). The IRGC runs unlicensed crypto mines that tap into the national power grid at a fraction of market rates, effectively stealing electricity to mine Bitcoin and other assets. This crypto mining sanctions evasion lets Iran generate hard currency despite tight international embargoes, and it also creates a massive energy drain that hurts ordinary citizens. Similar patterns appear in Russia, where state‑aligned groups commandeer botnets to launch DDoS attacks against foreign exchanges while simultaneously mining on compromised machines. China’s cyber units often embed backdoors in blockchain projects, giving them a foothold to exfiltrate data or manipulate token economics. Across these cases, the common denominator is a blend of strategic cyber pressure and illicit revenue streams, showing how state actors view the blockchain not just as a technology but as a financial battleground. These activities also expose weaknesses in blockchain security, from weak wallet implementations to inadequate network monitoring, prompting the wider crypto community to tighten defenses.
Understanding the mechanics of state‑sponsored hacking helps anyone involved in crypto stay one step ahead. First, recognize that government‑backed actors can afford sophisticated tools, so basic security hygiene—hardware wallets, multi‑factor authentication, and regular software updates—is non‑negotiable. Second, watch for signs of illicit mining, such as unexpected spikes in electricity usage or unexplained hash rate growth on public pools; these can indicate a nation‑state proxy at work. Third, stay informed about sanction regimes and how they may drive new attack vectors; when a country faces tighter financial pressure, its cyber campaigns often shift toward crypto‑focused revenue. By keeping these insights in mind, you can better assess risk, protect assets, and contribute to a more resilient blockchain ecosystem. Below you’ll find a curated set of articles that dive deeper into exchange reviews, mining scandals, regulatory impacts, and practical security tips—all tied back to the broader theme of state‑sponsored hacking.
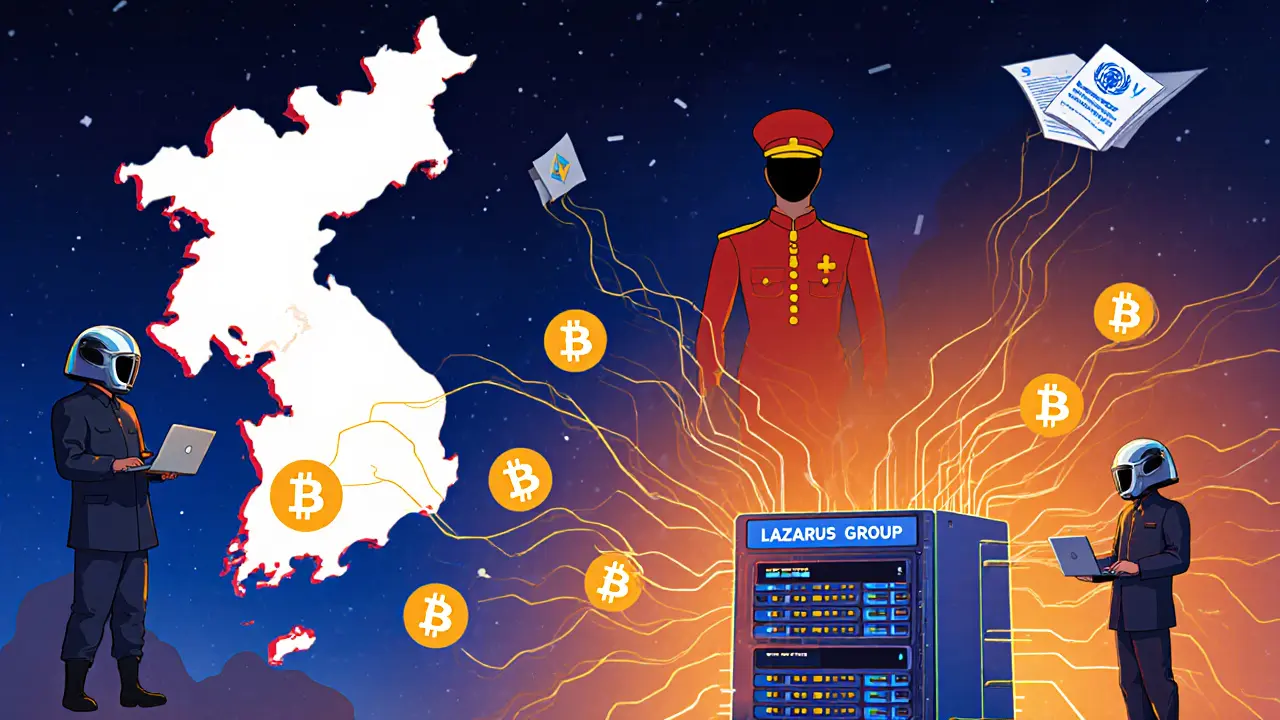
North Korea’s Crypto Ban & State‑Sponsored Hacking: 2025 Threat Overview
Explore how North Korea's 2025 crypto ban coexists with state‑sponsored hacking, the massive ByBit theft, laundering networks, and global responses to curb the threat.
- 17
- Read More