North Korea Crypto Hack: What You Need to Know
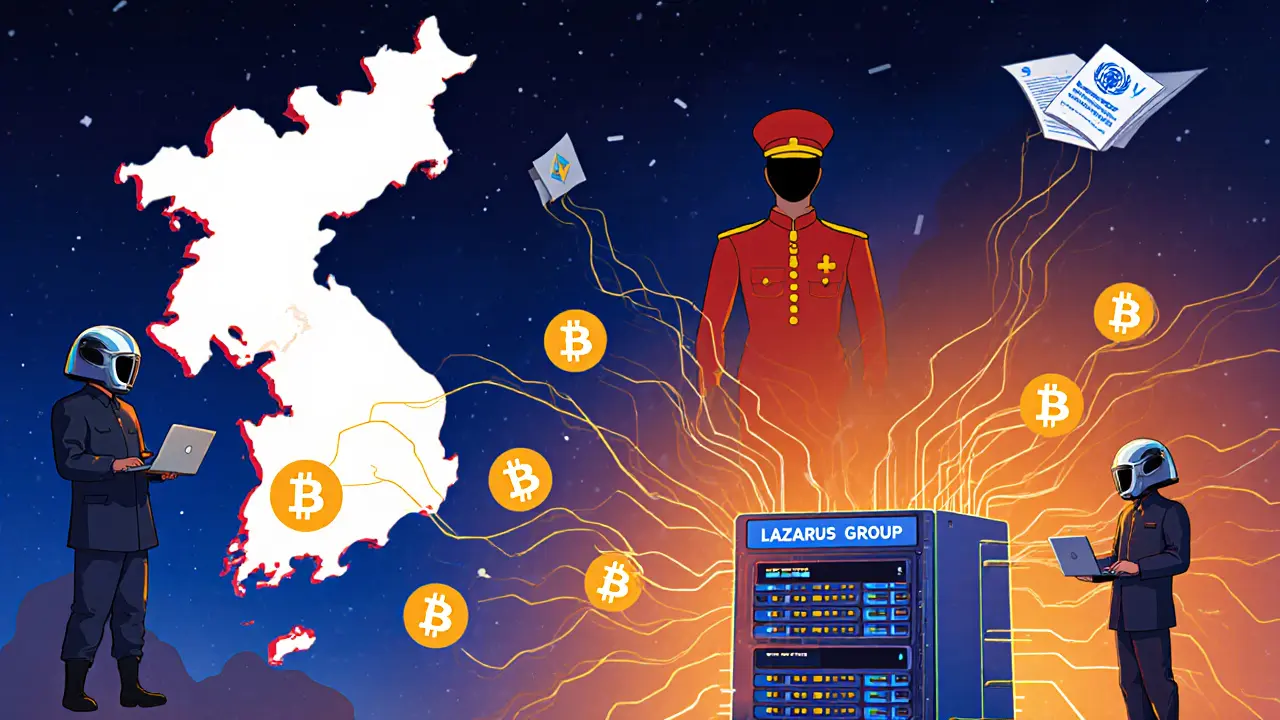
When talking about North Korea crypto hack, the large‑scale theft of digital assets attributed to the North Korean regime’s cyber units. Also known as NK crypto breach, it illustrates how a nation‑state blends advanced hacking skills with a desperate need for foreign currency.
Why the Hack Matters – Cybercrime, Sanctions Evasion, and Ransomware
The cybercrime, illegal activities performed through computers and networks behind the North Korea crypto hack is anything but random. State‑run groups such as the Lazarus Team deploy custom malware, phishing kits, and botnets to infiltrate exchanges, wallets, and DeFi protocols. This cybercrime platform enables three core actions: stealing private keys, moving funds through mixers, and cashing out via peer‑to‑peer platforms. Each step depends on sophisticated tools that hide the trail, making attribution a long‑term challenge.
At the same time, the operation serves as a work‑around for sanctions evasion, the practice of bypassing international financial restrictions. Because traditional banking channels are blocked, stolen crypto becomes a lifeline for purchasing luxury goods, securing foreign‑exchange contracts, and funding the regime’s weapons programs. The hack therefore links directly to broader geopolitical strategies – a clear example of how digital theft feeds state policy.
Ransomware attacks often act as a feeder into the larger theft pipeline. Victims who pay in Bitcoin or Monero after a ransomware hit unintentionally boost the volume that North Korean actors can launder. The hackers then use chain‑analysis evasion techniques, such as tumblers and privacy‑focused coins, to obscure the source. This creates a feedback loop: more ransomware payments mean more crypto to steal, and the stolen crypto funds further ransomware campaigns.
Tracking the flow of stolen assets relies on blockchain tracing, the analysis of public ledger data to follow transactions. Firms like Chainalysis and CipherTrace build graphs that highlight mixers, exchange deposits, and cross‑chain bridges. While the public ledger is immutable, the clever use of layered mixers can stretch a trace across dozens of hops, turning a single theft into a web of pseudonymous hops. Yet each successful trace adds pressure on the actors, forcing them to adopt newer obfuscation layers.
These four entities – cybercrime, sanctions evasion, ransomware, and blockchain tracing – interact in a tightly knit ecosystem. The North Korea crypto hack encompasses state‑sponsored theft, requires advanced malware tools, influences global ransomware economics, and drives the growth of blockchain forensic services.
Below you’ll find a curated set of articles that break down the surrounding crypto landscape. From exchange safety reviews and token analysis to tax reporting rules and DeFi fundamentals, each piece adds a piece to the puzzle of how digital money moves, who can protect it, and what regulators are doing to keep bad actors in check. Whether you’re a trader, developer, or simply curious about the security side of crypto, the collection gives you practical insights that complement the deep dive into the North Korea crypto hack.
North Korea’s Crypto Ban & State‑Sponsored Hacking: 2025 Threat Overview
Explore how North Korea's 2025 crypto ban coexists with state‑sponsored hacking, the massive ByBit theft, laundering networks, and global responses to curb the threat.
- 17
- Read More